SAML 2.0
When adding a SAML 2.0 identity provider (e.g. Shibboleth 2.0) the parameters listed below can be configured.
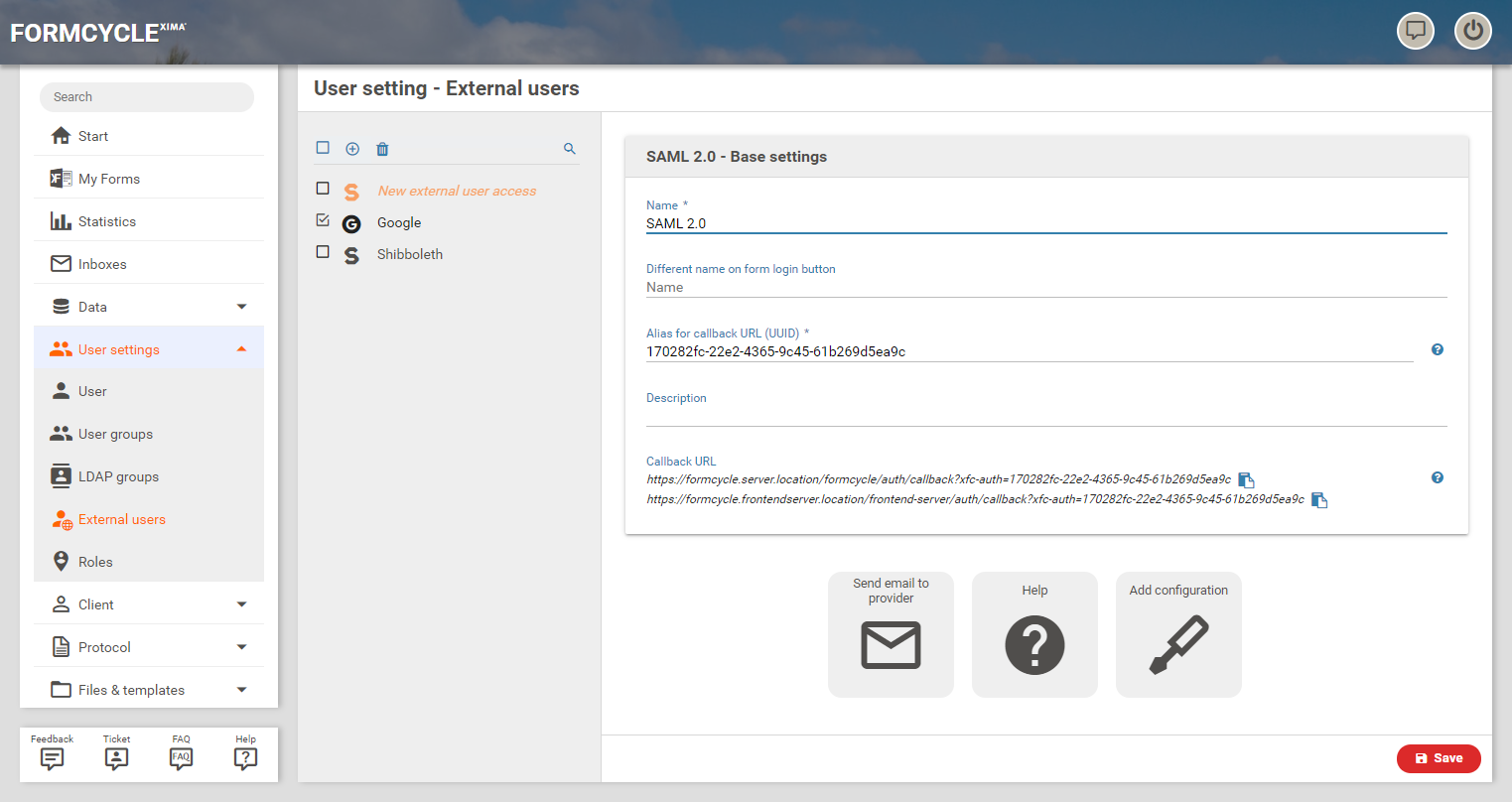
Base settings
Name
Name of the identity provider in Xima® Formcycle.
Different name on form login button
If a form has been configured to offer several authentication options, a dialog will be displayed when opening the form in which an authentication type has to be selected. The text content that should be on the button for this identity provider can be configured here.
If nothing is entered here, the name entered under Name is used.
Alias for callback URL (UUID)
Unique identifier that is used when the identity provider returns to Xima® Formcycle. This value is generated automatically, but can be changed if necessary.
Callback URL
URLs for each Xima® Formcycle-Server (master server as well as frontend servers) which can be used when returning from the identity provider to Xima® Formcycle. Each URL can be copied to the clipboard by clicking the copy icon to the right of the URL.
Initially visible buttons
Below the base settings there are initially 3 buttons whose functions are intended to help with the configuration of the Facebook identity provider.
Send email to provider
Opens the e-mail program set up in the system with a pre-formulated request regarding the information required for the configuration of the identity provider in Xima® Formcycle.
Help
Opens this help page in the browser.
Add configuration
If the required information has been provided by the identity provider, the area for the configuration of the identity provider can be opened by clicking on this button. Afterwards the area configuration which is described below opens.
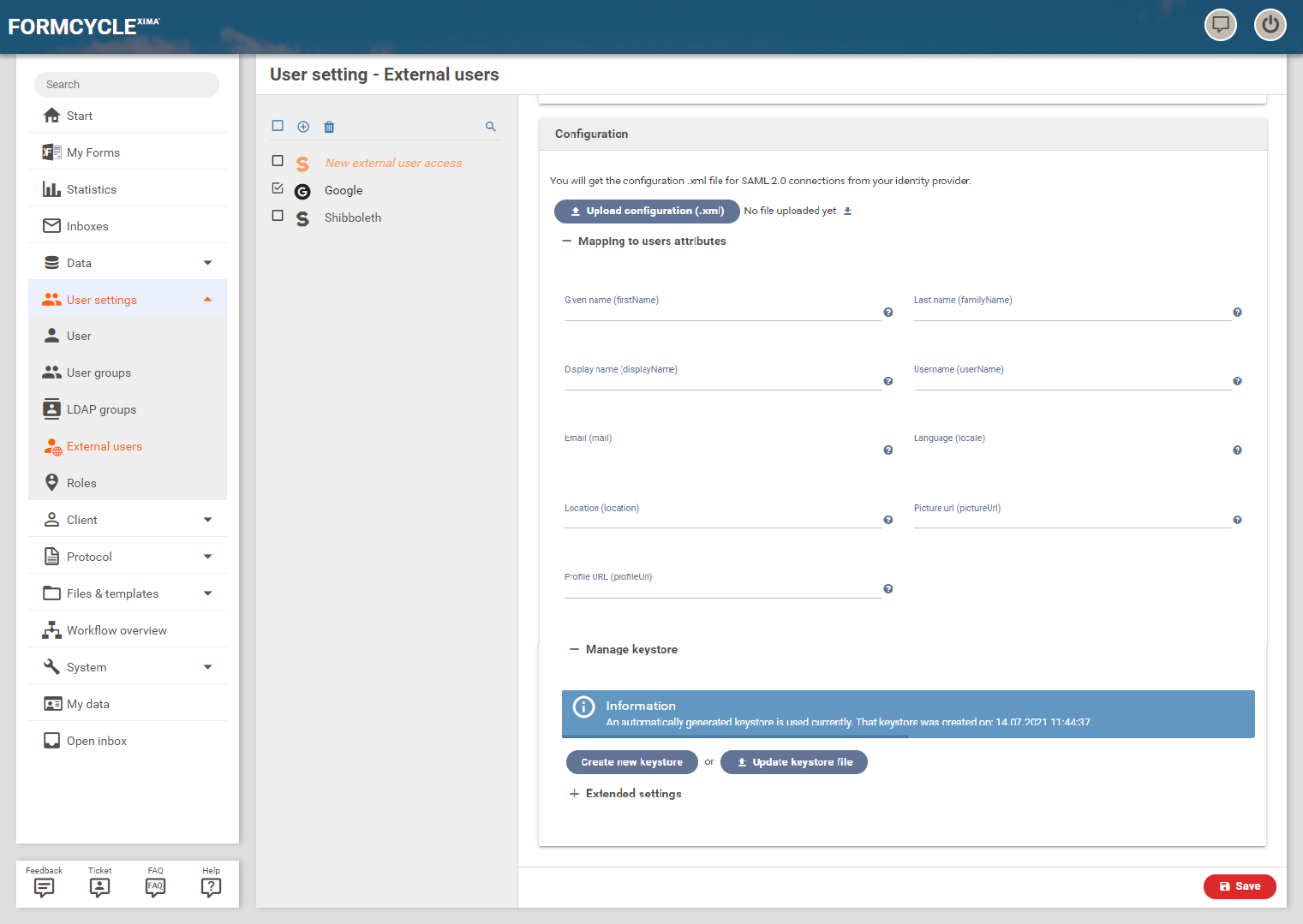
Configuration
- Upload configuration: Pressing this button opens a file selection dialog, with which the configuration file supplied by the Identity Provider can be selected. By confirming the selection in the dialog, the file is uploaded.
- FileName.xml: After a configuration file has been uploaded and the configuration was saved, it is possible to download the file here. The download is started by clicking on the file name or the symbol.
Mapping to user attributes
By clicking on Mapping to user attributes the configuration fields for mapping individual attributes can be made visible. SAML attributes can be configured for the following data. In each case, the name of the saml:attributes node must be specified.
- Given name (firstname): first name of the user
- Last name (familyName): Last name of the user
- Display name (displayName): Display name of the user
- Username (userName): User name of the user
- Email (mail): Email address of the user
- Language (locale): Language of the user
- Location (location): Location of the user
- Picture url (pictureUrl): Picture URL of the user
- Profile url (profileUrl): Profile URL of the user
Manage keystore
By clicking on Manage keystore the settings for the keystore become visible. There are the following two buttons:
- Create new keystore: Creates a new keystore with a new key pair
- Update keystore file: Opens a file selection dialog with which an existing keystore can be selected and uploaded.
After uploading your own keystore, the following input fields also appear:
- Keystore password: Password of the keystore
- Keypair password: Password of the key pair
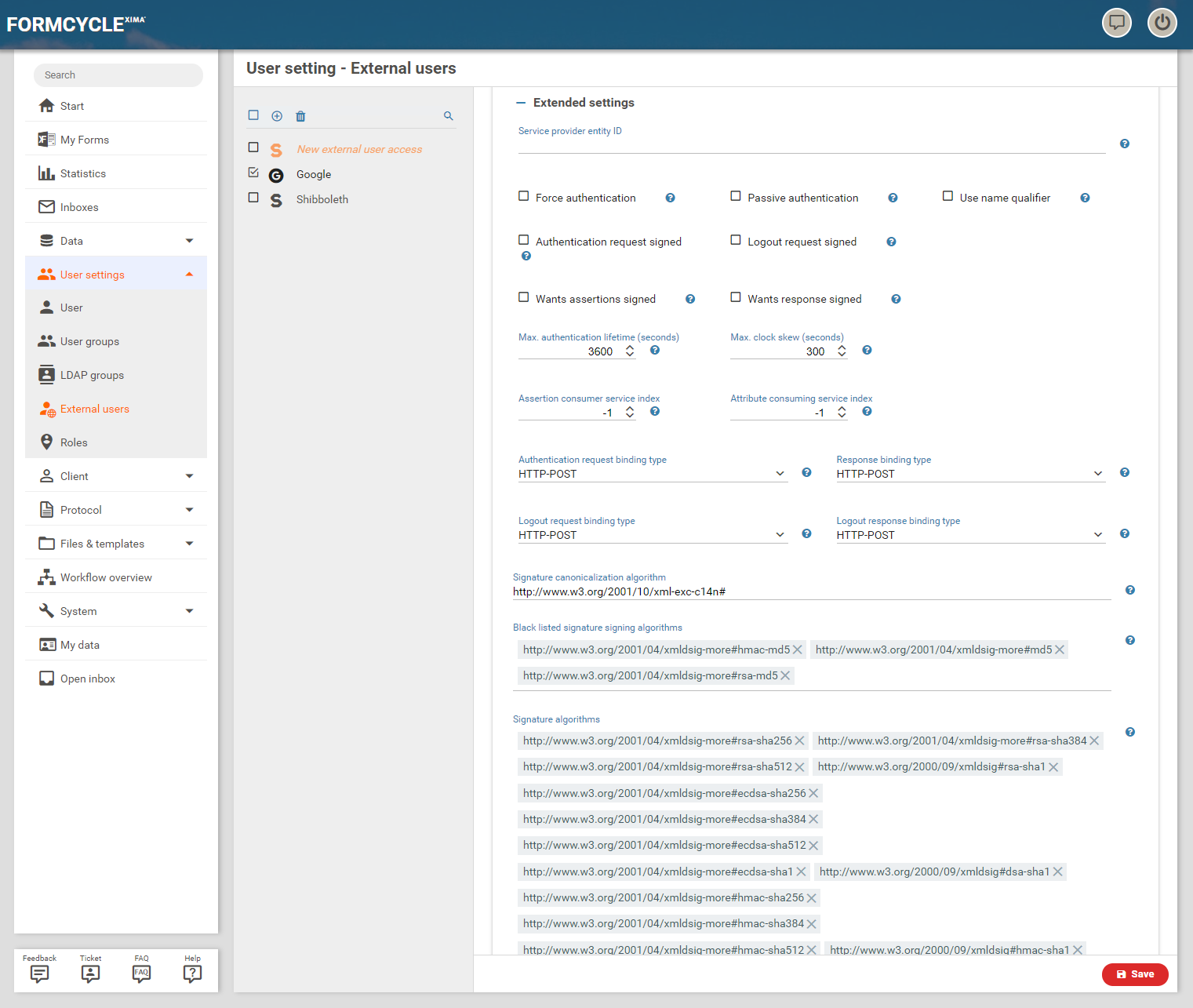
Extended settings
With a click on Extended settings further parameters for the connection with the Identity Provider can be configured.
Service provider entity ID
Optional ID for identification against the Identity Provider.
Force authentication
Specifies whether a user should be forced to log in even if a valid session is still present.
Passive authentication
Specifies whether an authentication without interaction with the user should be tried.
User name qualifier
Specifies whether the authentication request should also send the NameQualifier. This is not required by the SAML standard, but for some identity providers it is necessary.
Authentication request signed
Specifies whether the authentication request should be digitally signed.
Logout request signed
Specifies whether the logout request should be digitally signed.
Wants assertions signed
Specifies whether the SAML statements (assertions) are requested to be digitally signed.
Wants response signed
Specifies whether the SAML responses should be digitally signed.
Max. authentication lifetime (seconds)
Maximum duration of an exisitng login to the identity provider. The default value is 3600 seconds.
Max. clock skew (seconds)
Maximum allowed difference in system clock times between the Xima® Formcycle Server and the identity provider. The default value is 300 seconds.
Assertion consumer service index
Specifies the index of the Assertion Consuming Service to be used in the login request. The default value is -1, which is the default of the identity provider.
Attribute consumer service index
Specifies the index of the attribute consuming services which should be used for the authentication request. The default value is -1, which is the default of the identity provider.
Authentication request binding type
Specifies the transmission type with which Xima® Formcycle requests a login to the identity provider.
Response binding type
Specifies the transmission type with which the identity provider responds to a Xima® Formcycle login.
Logout request binding type
Specifies the transmission type with which Xima® Formcycle requests a logoff from identity provider.
Logout response binding type
Specifies the transmission type with which the identity provider responds to a logoff from Xima® Formcycle.
Signature canonicalization algorithm
Specifies the algorithm to be used to convert the signed request into a standardized XML form. http://www.w3.org/2001/10/xml-exc-c14n# is used by default.
Black listed signature signing algorithms
Algorithms that are forbidden for signing.
Signature algorithms
Algorithms allowed for signing.
Signature reference digest methods
Specifies the hash algorithms that are allowed when signing the SAML statements (assertions).
Download service provider metadata
By clicking on this button, the service metadata is generated as XML based on the previously specified settings and made available as a download.
This metadata can then be integrated directly into the respective identity provider.