OpenID Connect
When adding a OpenID Connect identity provider the following parameters are requested:
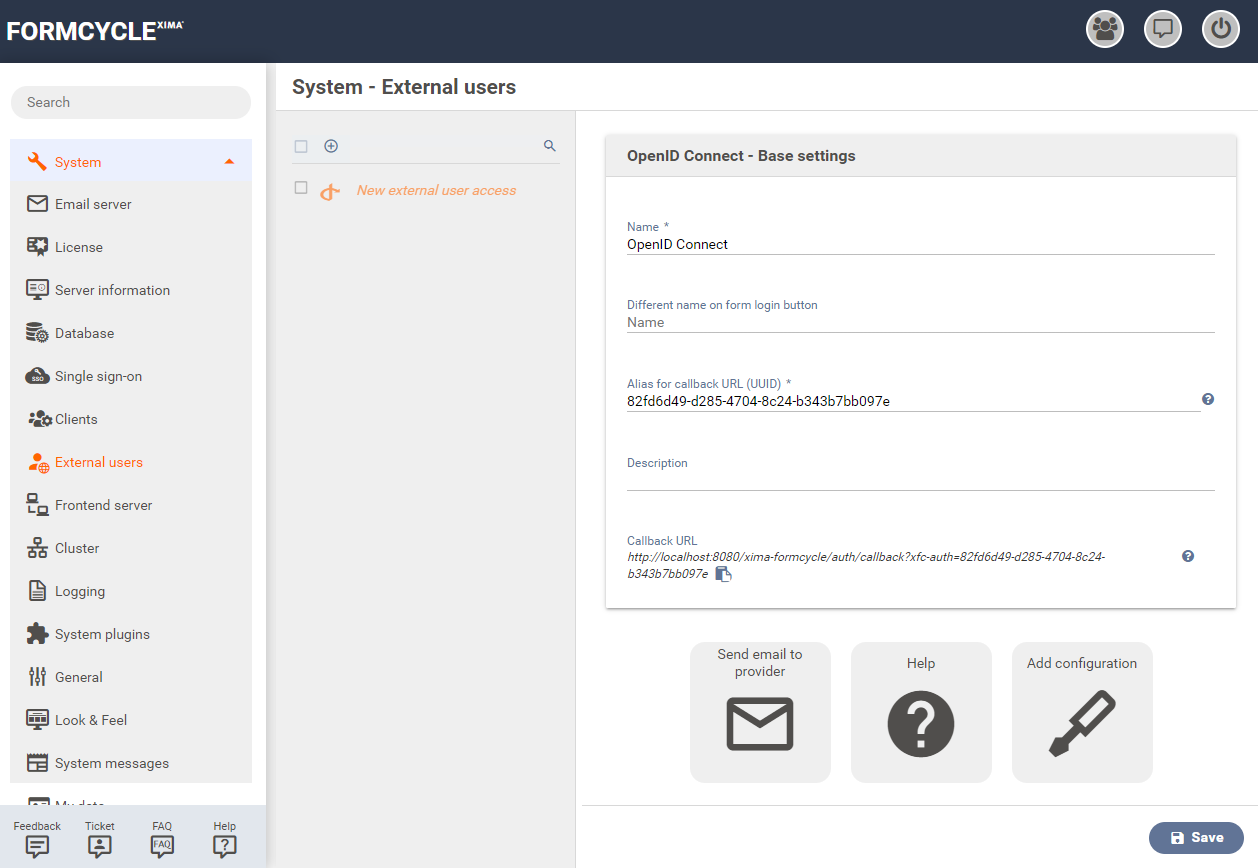
Base settings
Name
Name of the identity provider in Xima® Formcycle.
Different name on form login button
If a form has been configured to offer several authentication options, a dialog will be displayed when opening the form in which an authentication type has to be selected. The text content that should be on the button for this identity provider can be configured here.
If nothing is entered here, the name entered under Name is used.
Alias for callback URL (UUID)
Unique identifier that is used when the identity provider returns to Xima® Formcycle. This value is generated automatically, but can be changed if necessary.
Callback URL
The URL which is used when returning from the identity provider to Xima® Formcycle is shown here and can be copied to the clipboard by clicking the copy icon to the right of the URL.
Initially visible buttons
Below the base settings there are initially 3 buttons whose functions are intended to help with the configuration of the Facebook identity provider.
Send email to provider
Opens the e-mail program set up in the system with a pre-formulated request regarding the information required for the configuration of the identity provider in Xima® Formcycle.
Help
Opens this help page in the browser.
Add configuration
If the required information has been provided by the identity provider, the area for the configuration of the identity provider can be opened by clicking on this button. Afterwards the area configuration which is described below opens.
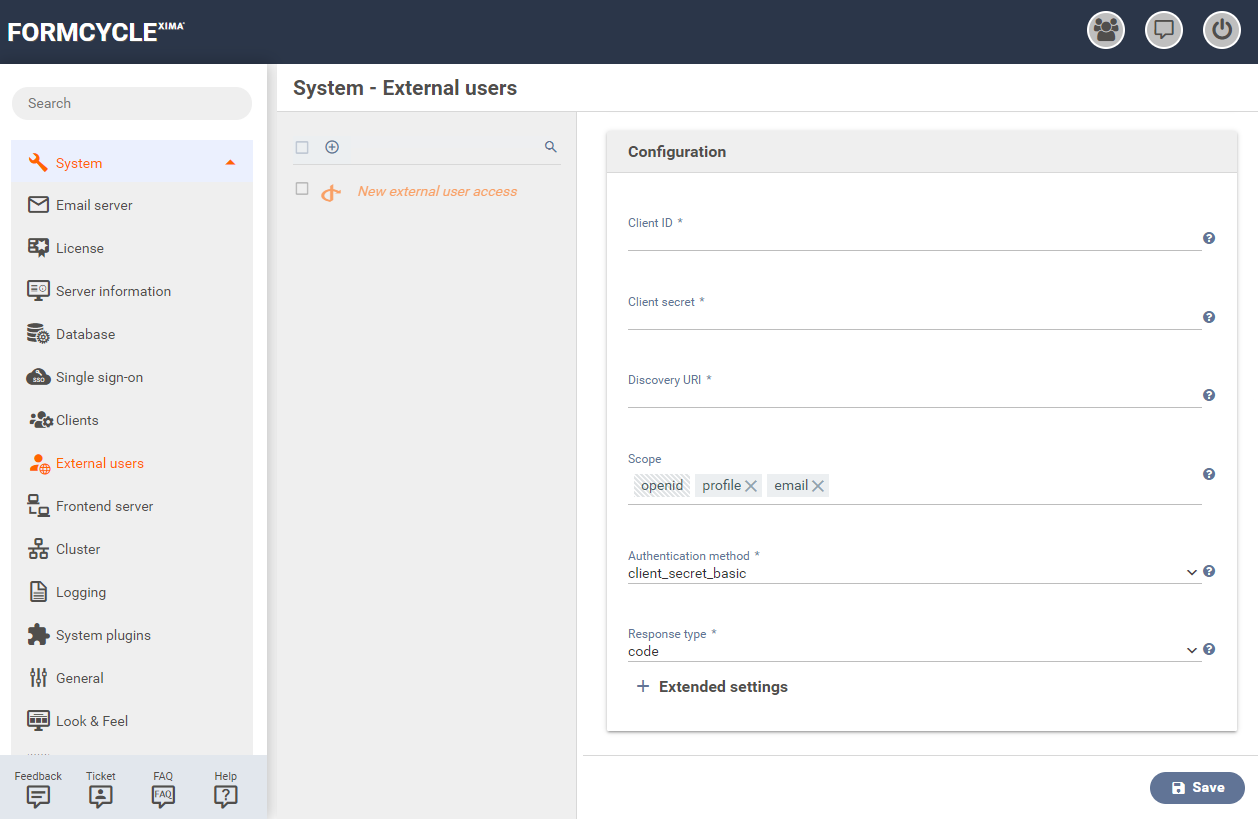
Configuration
Client ID
Unique ID of the configuration that is provided by the identity provider.
Client secret
Secret key which is used to authenticate your client.
Discovery URI
URI which is used to determine the properties of the identity provider. It has to be provided by the identity provider.
Scope
Specifies the permissions that are used by Xima® Formcycle when querying fields from the identity provider.
Authentication method
Method by which Xima® Formcycle authorizes itself to the identity provider.
Response type
Type of response from the identity providers after Xima® Formcycle logon.
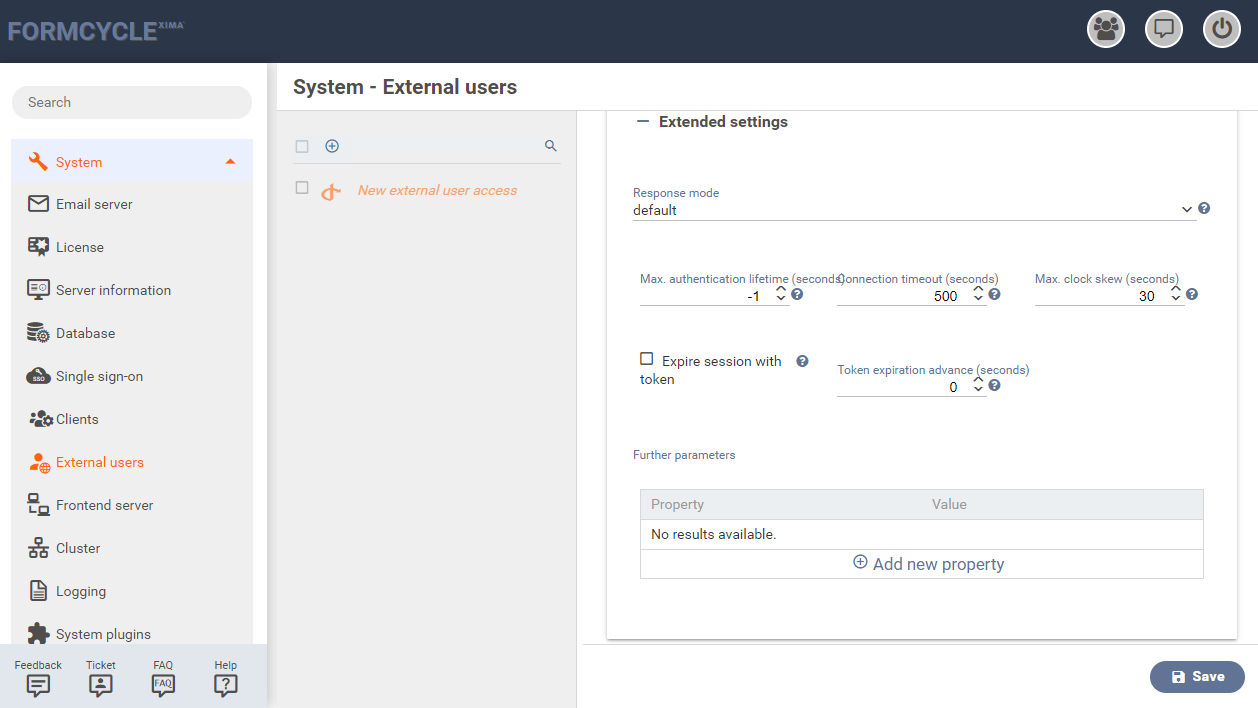
Extended settings
By clicking on Extended settings additional parameters for the connection with the identity provider can be configured.
Response mode
Method by which the identity provider sends the logon respone to Xima® Formcycle.
Max. authentication lifetime (seconds)
Maximum duration of an exisitng login to the identity provider. The default value is -1, which means infinite.
Connection Timeout (seconds)
Maximum duration for a connection setup to the indentity provider before it is terminated. The default value is 500 seconds.
Max. clock skew (seconds)
Maximum allowed difference in system clock times between the Xima® Formcycle Server and the identity provider. The default value is 30 seconds.
Expire session with token
Setting that specifies whether a Xima® Formcycle logon should also expire when the identity provider logon expires. This option is disabled by default.
Token expiration advance (seconds)
Time period that a Xima® Formcycle logon should expire before the identity provider token. The default value is 0 seconds.
Further parameters
In addition to the ones listed above, other parameters can be defined in this table. A property and a corresponding value must be entered in each line.
Direct client activated (HTTP header)
7.4.0+ If activated, a direct OpenId Connect client will be available. A Direct OpenId Connect client performs its authentication logic directly on the request to a protected resource (e.g. the form) by analyzing request headers with JWTs (JSON Web Token) (see below).
Direct client activated (Cookie)
7.4.0+ If activated, a direct OpenId Connect client will be available. A direct OpenId Connect client performs its authentication logic directly on the request to a protected resource (e.g. the form) by analyzing the transmitted cookies with JWTs (JSON Web Token).